Don't let leaked content destroy your privacy, reputation, or business.
Leaked content can ruin reputations, violate privacy, or bankrupt your digital product business — in a single day. Whether it’s stolen personal media, leaked OnlyFans content, private client material, or pirated courses, ContentRemoval continuously scans the internet to alert you the moment it appears.
Take back control→Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


Malala Leides


Phil Graham


William Brown


Alex Hormozi


Ahmed Ben Chaibah


Alan Graves


Alex Fedotoff


Laurence Thomas


Why is leaked content so damaging?
Leaks spread incredibly fast and often anonymously. Your only real chance to contain them is early detection and fast takedown. Too often, leaked content goes unnoticed and: 💔 Destroys personal reputations, especially in cases of intimate or explicit leaks 💰 Tanks online course and subscription revenue 🔏 Violates contracts or NDA's, triggering legal & financial risk 👑 Damages your brand's authority if proprietary materials go public 💬 Erodes trust by exposing private conversations or client information
Get Started→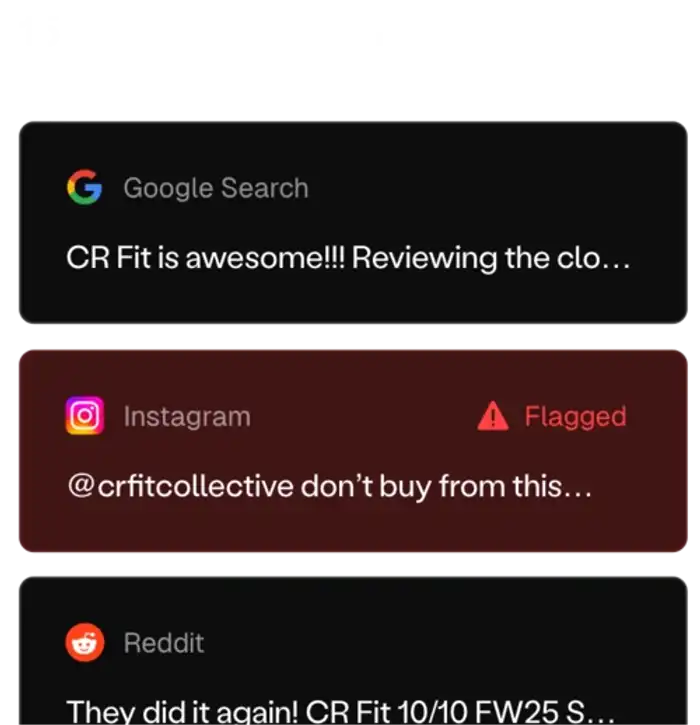
Manual detection simply doesn't work.
From leaked sex tapes to stolen course files — your content should not be in the wrong hands. ContentRemoval gives you full visibility, fast detection, and the tools to fight back.
We fix that→Trying to do this yourself? Here's what you're up against:
Private Networks
💬
Leaked content spreads in private groups and obscure platforms.
Duplicate Content
🪞
You won’t find mirror links, torrents, or reposts manually.
No Alerts
🔕
You won't get alerts - so you only find it after others do.
Doesn't Scale
📉
You can't track leaks at scale across all platforms.
Imperfect Matches
✍️
You'll miss non-exact matches of slightly renamed or edited content.
Constant Updates
🔄
Leakers frequently move and re-upload content.
Whether it's personal or professional... you deserve control of your content.
The longer leaked content is live, the more copies exist — and the harder it is to erase. And once it’s out there, it can spiral across platforms in minutes. With ContentRemoval, nothing slips through.
Get Started→Real-time Alerts
🔔
Monitor Piracy
🏴☠️
Monitor Adult Content
🔞
Collect Evidence For Legal Use
🔖
Full search index logging
🔎
And so much more...
🛡️
Get started in 2 minutes
No complex tools. No bloated dashboards. Just clear insights when and where it matters.
Start Monitoring Now→Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
Defamation
Hate Speech
Copyright Infringement
Trademark Infringement
Personal Data
Cyber Abuse
Revenge Porn
Legal Proceedings
Outdated Content
Identity Theft
Privacy Violations
Harassment
Impersonation
Doxxing
Explicit Content
Cyberstalking
Competitor Attacks
Digital Products
Unauthorized Use
 Google
Google Yahoo
Yahoo Bing
Bing DuckDuckGo
DuckDuckGo Baidu
Baidu Instagram
Instagram Facebook
Facebook Reddit
Reddit X / Twitter
X / Twitter Blogger
Blogger YouTube
YouTube TikTok
TikTok Pinterest
Pinterest LinkedIn
LinkedIn Vimeo
Vimeo Tumblr
Tumblr Alex Hormozi
Alex Hormozi Sweat.com
Sweat.com Saski Collection
Saski Collection Defamation
Defamation Revenge Porn
Revenge Porn